0x41haz
Published:
THM 0x41haz
The binary was equipped with anti reversing techniques. Running the files command gives the following output.
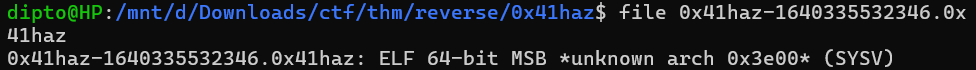
We need to fix that. If we check the hexdump of the binary, we can see the following:
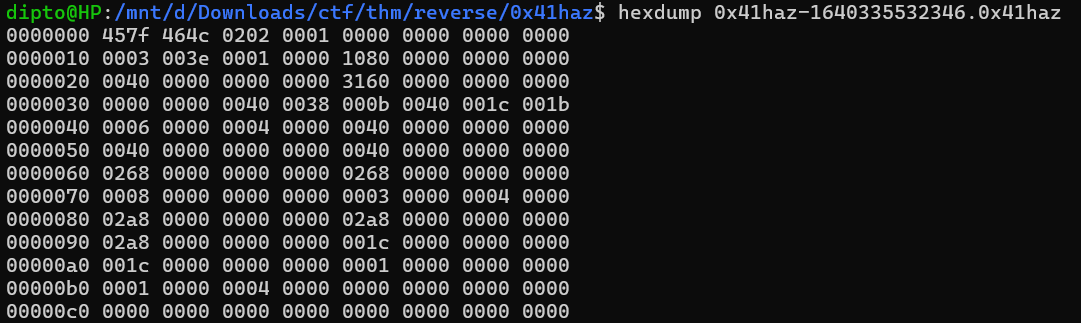
Here, we see that the 6th byte is set to 0x01. If we check the ELF header signature, we see that, 6th byte needs to be set to 0x01 for the original and current version of ELF.
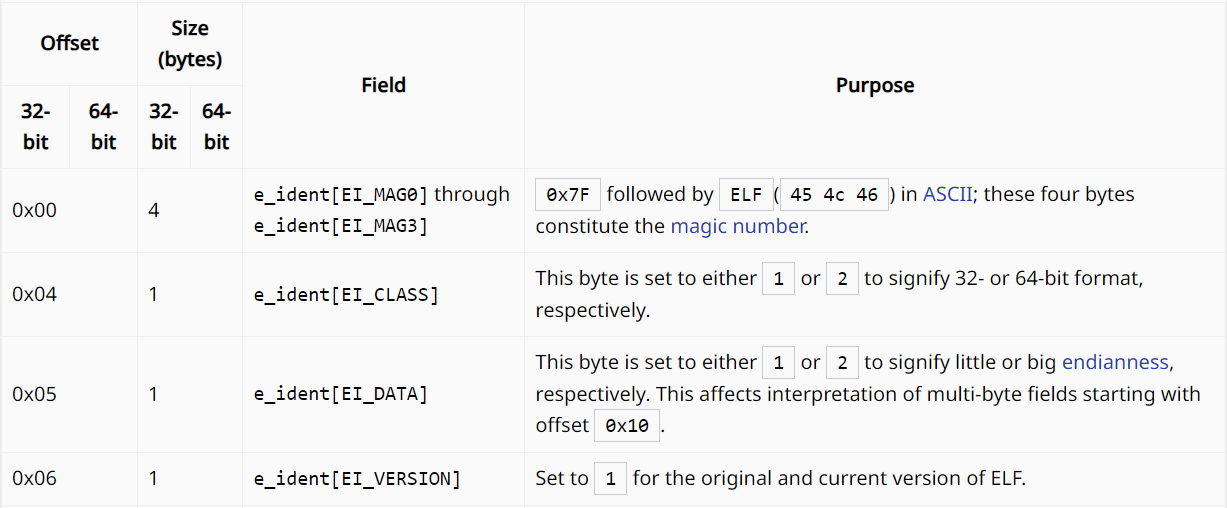
Updating the 6th byte from 02 to 01, we get the following output:
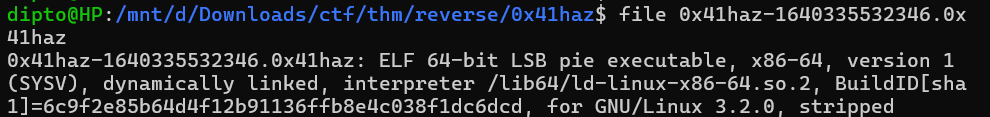
Now, the binary can be run and debugged.
Opening the binary in ghidra, we can see the following decompiled function which is interesting:
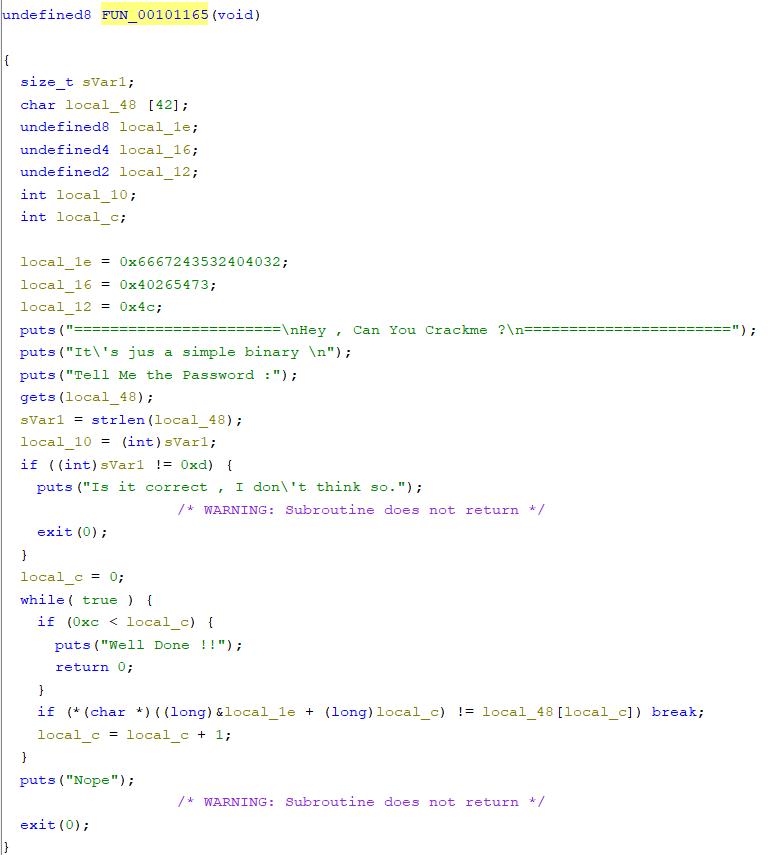
We can see that the password is 13 digits long. The byte checking inside the while loop checks the bytes of the input and the byte at address local_1e+local_c. The address local_1e contains the last byte that is allocated, i.e. the values are going to be checked in reverse order. The structure of the stack frame is like below:
| Return Address | 8 bytes |
|---|---|
| local_c | 4 bytss |
| local_10 | 4 bytes |
| local_12 | 2 bytes |
| local_16 | 4 bytes |
| local_1e | 8 bytes |
| local_48 | 42 bytes |
| sVar1 | 8 bytes |
So, if we construct the correct input, the value we get is: 0x3240403235246766735426404c. (Concatenating local_1e,local_16and local_12). Converting this long value to bytes, we get the correct password: 2@@25$gfsT&@L. So. our flag is: THM{2@@25$gfsT&@L}
